Compliance Assessment is one of the TOGAF deliverables you can create with the TOGAF tool.
Once an architecture has been defined, it is necessary to govern that architecture through implementation to ensure that the original Architecture Vision is appropriately realized and that any implementation learnings are fed back into the architecture process. Period compliance reviews of implementation projects provide a mechanism to review project progress and ensure that the design and implementation is proceeding in-line with the strategic and architectural objectives.
Step 1: Describe Compliance Assessment Overview
Provide an overview of compliance assessment
Provide an overview on the compliance assessment. Describe the project’s progress and status, and project’s architecture/design.
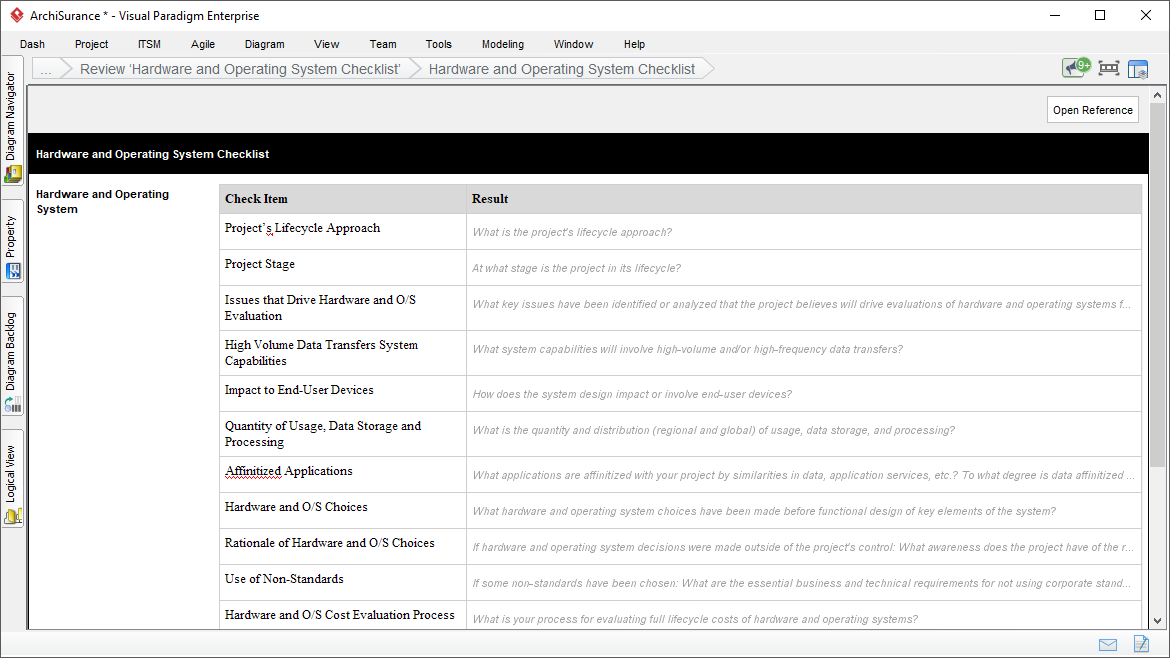
Step 2: Review ‘Hardware and Operating System Checklist’
Review ‘Hardware and Operating System Checklist’
The Architecture Compliance Review Checklist provide a wide range of typical questions that may be used in conducting Architecture Compliance reviews, relating to various aspects of the architecture.
In this step, you are required to perform architecture review based on the Hardware and Operating System Checklist, and document the result.
Step 3: Review ‘Software Services and Middleware Checklist’
Review ‘Software Services and Middleware Checklist’
Perform architecture review based on the Software Services and Middleware Checklist, and document the result.
Step 4: Review ‘Applications Checklist’
Review ‘Applications Checklist’
Perform architecture review based on the Applications Checklist, and document the result.
Step 5: Review ‘Information Management Checklist’
Review ‘Information Management Checklist’
Perform architecture review based on the Information Management Checklist, and document the result.
Step 6: Review ‘Security Checklist’
Review ‘Security Checklist’
Perform architecture review based on the Security Checklist, and document the result.
Step 7: Review ‘System Management Checklist’
Review ‘System Management Checklist’
Perform architecture review based on the System Management Checklist, and document the result.
Step 8: Review ‘System Engineering Checklist’
Review ‘System Engineering Checklist’
Pperform architecture review based on the System Engineering Checklist, and document the result.
Step 9: Review ‘Methods and Tools Checklist’
Review ‘Methods and Tools Checklist’
Perform architecture review based on the Methods and Tools Checklist, and document the result.